In medicine, the difference between life and death often depends on how fast and accurately you can process evidence, rule out threats, and apply the right intervention. As a former paramedic turned cybersecurity professional, I’ve carried this mindset with me into the Security Operations Center (SOC), where the stakes are digital — but the thinking is just as critical.
The Evidence Pyramid in Medicine
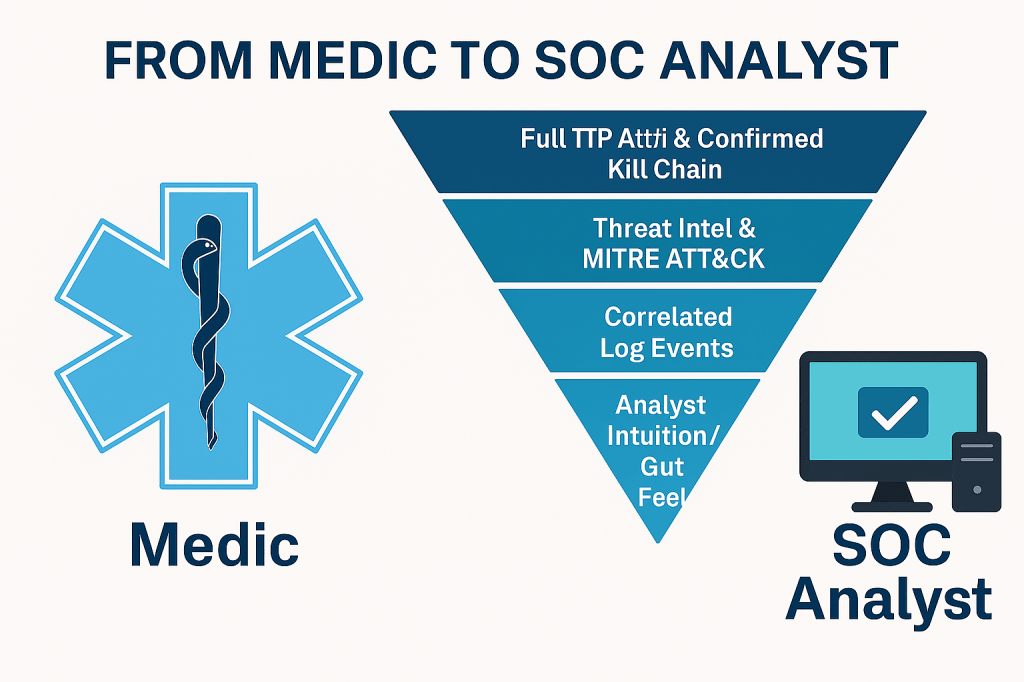
In clinical reasoning, practitioners often work through the evidence pyramid in reverse — starting from broad symptoms and subjective observations and narrowing toward the most reliable, evidence-based diagnosis. While traditionally visualized upright, we use it mentally as an upside-down pyramid to guide decision-making.
At the widest part of the inverted structure, you begin with personal experience and expert opinion. As you progress downward, the evidence becomes stronger and more focused — including case studies, cohort research, and culminating in systematic reviews and meta-analyses. This process helps medics prioritize action: starting with observable symptoms, ruling out possibilities through targeted diagnostics, and escalating interventions based on the most reliable evidence.
Translating the Evidence Pyramid to Cybersecurity
In cybersecurity, we often rely on Indicators of Compromise (IoCs), threat intelligence, behavioral analytics, and pattern recognition to make decisions. The correlation to the medical evidence pyramid is striking:
- Analyst Intuition / Gut Feel = Expert opinion
- Past Incidents / Case Studies = Clinical case reports
- Correlated Log Events = Observational studies
- Threat Intel & MITRE ATT&CK = Peer-reviewed studies
- Full TTP Attribution & Confirmed Kill Chain = Meta-analysis-level certainty
In both domains, you’re narrowing down from broad symptoms (“Something’s wrong”) to a specific, evidence-based diagnosis (“This is credential theft via lateral movement”) and tailoring your response accordingly.
Incident Triage as Digital Diagnosis
As a medic, I used the evidence pyramid to:
- Observe symptoms
- Rule out non-life-threatening conditions
- Confirm a likely cause
- Start the least invasive intervention
- Escalate based on patient deterioration
Now, in the SOC, I:
- Detect suspicious behavior (e.g., abnormal logins)
- Rule out benign causes (e.g., user on VPN)
- Correlate across multiple systems (logs, alerts, packets)
- Respond minimally (monitor, alert, isolate)
- Escalate as the threat progresses (containment, IR handoff)
Why This Makes Me an Asset
This approach means I don’t chase every alert — I triage with discipline. I prioritize threats based on likelihood and severity. I create detection content that reflects actual attacker behaviors, not just IOCs. I understand that response should be measured, layered, and intentional — just like in emergency medicine.
I’ve brought these skills to my current work in AI-powered risk reporting and threat intelligence. Trusted with a high volume of mission-critical tasks and cross-functional support due to proven reliability and subject-matter strength, guided tooling improvements, and communicated threat posture clearly and quickly — all while holding Security+, CySA+, and CSAP certifications.
In Summary
I didn’t leave medicine behind. I brought it with me — and that mindset is now protecting critical infrastructure.
If you’re looking for a cybersecurity analyst who triages like a medic, thinks like a threat actor, and executes like an operator — let’s talk. Because I don’t just want to join your team.
I want to fortify it.
Leave a comment